|
|
|
You might wonder why the order of the days is reversed. The reason is quite simple. The officer, responsible for handing out the key for that day, could tear off the current day at the bottom of the sheet and give it to the radio operator to set the machine. After being used, the strip of paper with the key was destroyed.
The Kenngruppen 
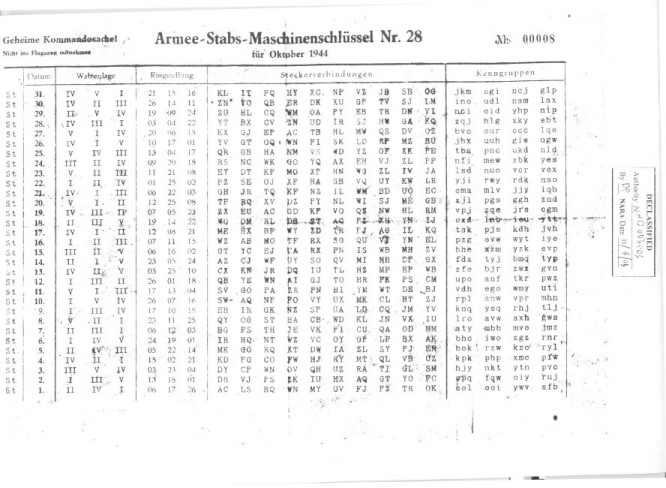
To identify the key that was used for a particular message, the operator had to insert a five-letter group called Buchstabenkenngruppe (letter identification group) as the first group of the message. The Buchstabenkenngruppe is composed of two randomly selected letters and one of the four possible three-letter Kenngruppen at the key sheet for that day. If we take day 31 from the Army Staff key 28 (image above), we see the Kenngruppen JKM, OGI, NCJ and GLP. In this case, some examples of a correct Buchstabenkenngruppe are FDJKM, KVOGI or QNNCJ.
This five-letter group at the start of the message should not be encrypted with the rest of the message! If a message was divided into several parts, the operator had to insert another Buchstabenkenngruppe for each part of the message. When counting the letters for the message header, the five letters of the Buchstabenkenngruppe must be included. The receiving operator immediately recognized which key was to be applied by looking at the last three letters of the first group.
The Message Key 
The settings of the machine were typically valid for one day. Using the same settings for a large number of messages would increase the statistical amount of data to break a particular key. Therefore, each message was sent with a different start position of the Enigma rotors, randomly selected by the operator. This was called the Spruchschlüssel or message key.
Until 1940, the German Army used other key sheets as those shown above. The first version contained a start position (Grundstellung) for each day. The operator chose a random message key and, with the rotors in the daily start position, he encrypted the message key twice to exclude errors. As example, we assume the trigram GHK was encrypted twice, resulting in XMC FZQ (fictitious example result). Next, the operator moved the rotors to the message key GHK and encrypted the message. The two trigrams, being the encrypted message key, were transmitted, together with the message.
The receiver sets his rotors at the daily start position, as described in the key sheet, and decrypts the trigrams XMC FZQ back into the GHK GHK message key. Next, he sets the message key GHK as start position on his machine and decrypts the actual message. However, this procedure was actually a security flaw. The message key is encrypted twice, resulting in a relation between first and fourth, second and fifth, and third and sixth character. Moreover, many message keys on a particular day would have the same setup and start positions. This security problem enabled the Polish Cipher Bureau to break the pre-war Enigma messages. However, German cryptologists were aware of the security flaw.
From 1940 on, the Wehrmacht changed the message key procedures to increase security. As before, the Wehrmacht radio operator sets each day the rotors, ring settings and plugboard according to the key sheet. For each new message, he now selects new randomly chosen start position or Grundstellung, say WZA, and a random message key or Spruchschlüssel, say SXT. He moves the rotors to the random start position WZA and encrypts the random message key SXT. With the above key of 31 October 1944 this will give RSK.
He then sets message key SXT as start position of the rotors and encrypts the actual message. Next, he transmits the random start position WZA, the encrypted message key RSK and the Kenngruppe FDJKM together with his message.
Example of the typical Wehrmacht message:
|
The message was created at 12h30, consists of three parts (3 teile), of which this is the first (1 teil), and contains 180 characters (Buchstabenkenngruppe included). The Buchstabenkenngruppe FDJKM shows the operator that the key settings, used to encrypt the message, was the one with Kenngruppe JKM from 31 October 1944.
The receiver sets the rotor start position according the first trigram WZA and decrypts the second trigram RSK to retrieve the message key SXT. Next, he uses the message key SXT as rotor start position to decrypt the actual message, skipping the first group FDJKM (the Kenngruppe). If a message was divided into several parts, the operator had to insert a new random start position and encrypted message key for each part of the message.
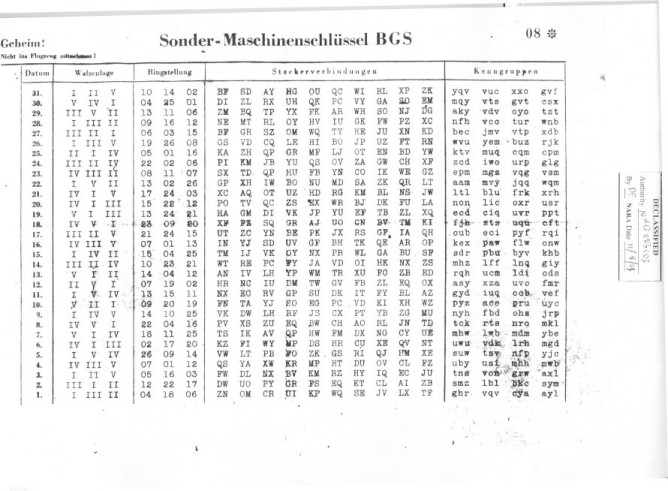
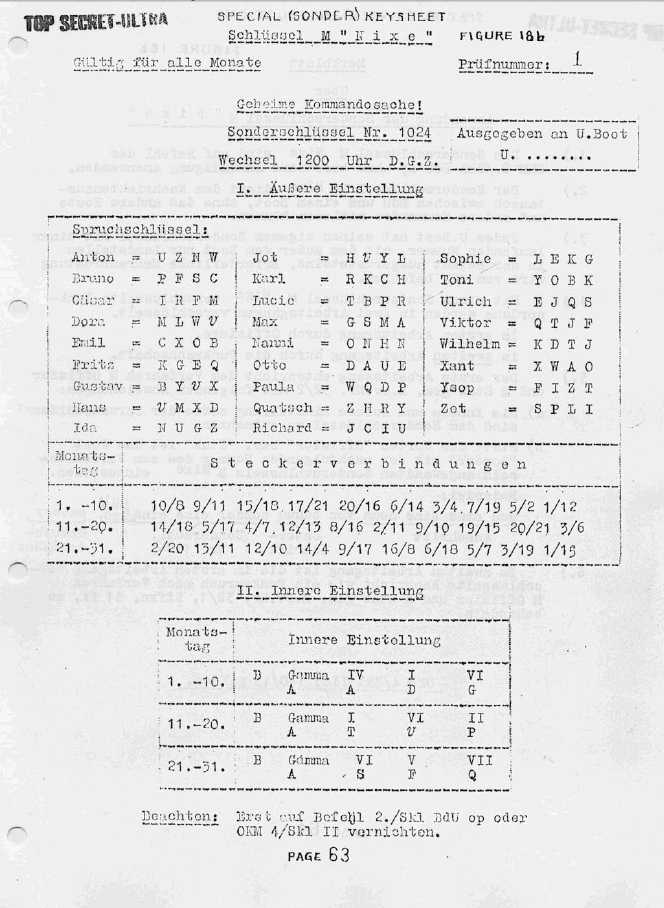
The Kriegsmarine Procedures 
To reduce the risk of cryptanalysis, the Kriegsmarine (German Wartime Navy) limited the use of the same key sheets. They designated many smaller radio net areas, each with its own codename and Enigma key sheets. HEIMISCHE GEWÄSSER (named Dolphin by the Bletchley Park codebreakers) was the first general naval key, later replaced by HYDRA. TRITON (Shark) were the U-boats in the Atlantic and Mediterranean, with the Mediterranean U-boat keys later replaced by MEDUSA (Turtle). The U-boats in the north had NIOBE (Narwhale), the Black Sea POSEIDON (Grampus) and in the Far East TIBET (Sunfish).
The Kriegsmarine procedures on sending messages with the Enigma cipher machine were far more complex and elaborate than the Heer and Luftwaffe procedures. The Kriegsmarine Enigma key sheets consisted of two parts.
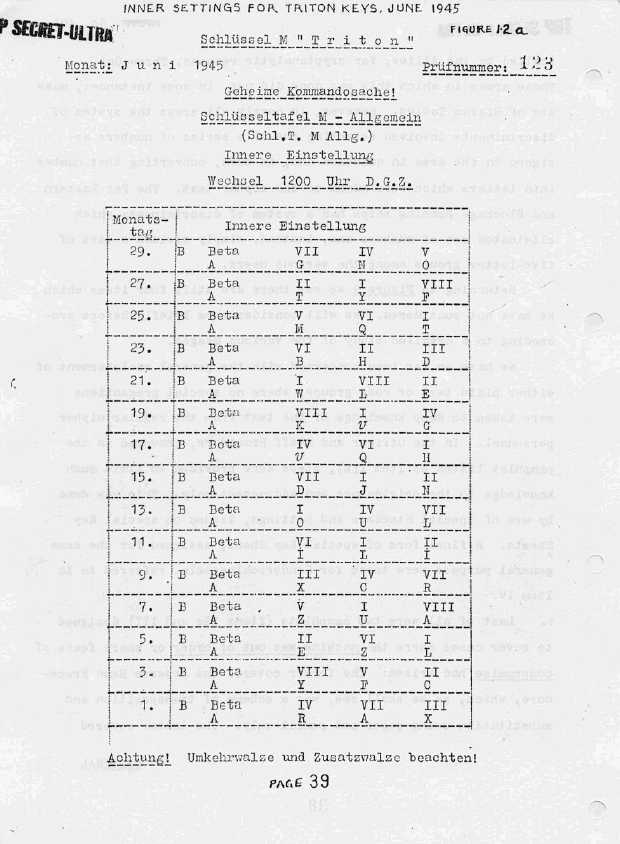
- Schlüsseltafel M Allgemein - Innere Einstellung (internal settings), contained the three rotors and their ring settings, the thin beta or gamma rotor and the reflector, and this only for the odd days of a month.
- Schlüsseltafel M Allgemein - Aussere Einstellung (external settings), contained the plugs and Grundstellung (basic start position) for each day of the month.
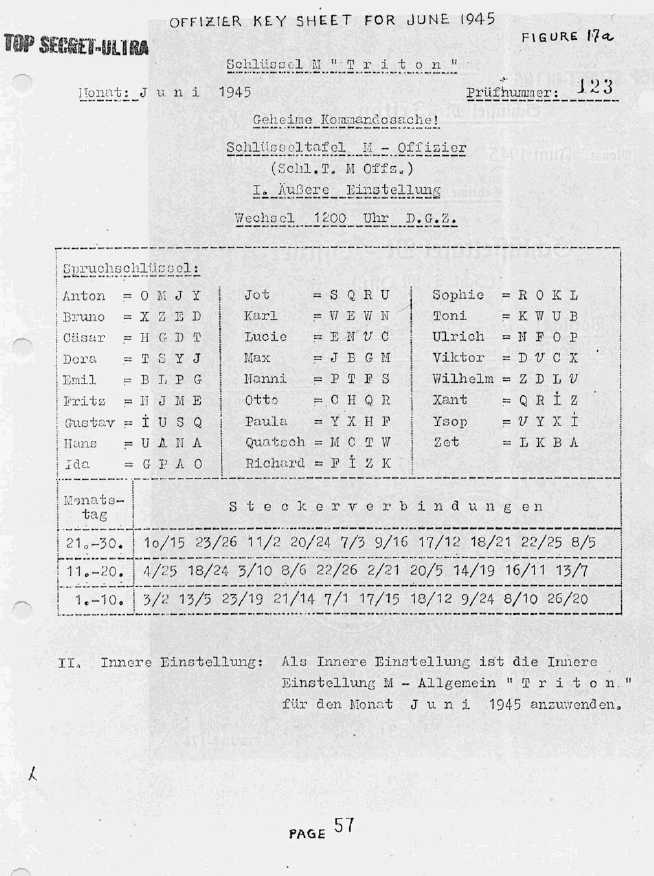
An additional key existed for the officers and a special Schlüssel M NIXE was used for private communication between the captain and U-boat Command, without other U-boats being able to read the message.
Examples of Kriegsmarine TRITON keys and Sonderschlüssel (special key) NIXE (click to enlarge).
Copyrighted Images, courtesy Frode Weierud![]()
Kriegmarine Kenngruppen 
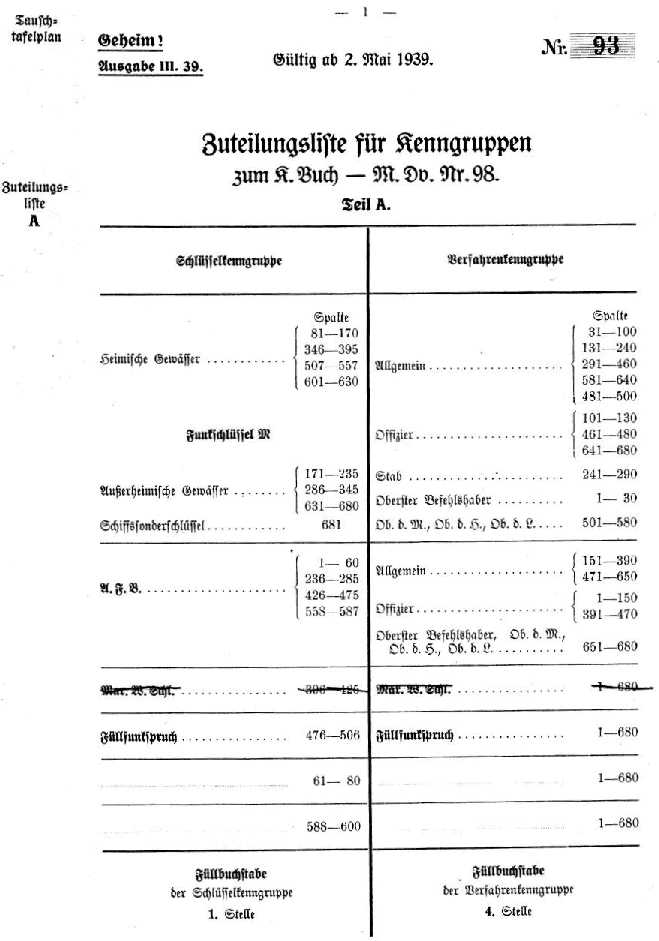
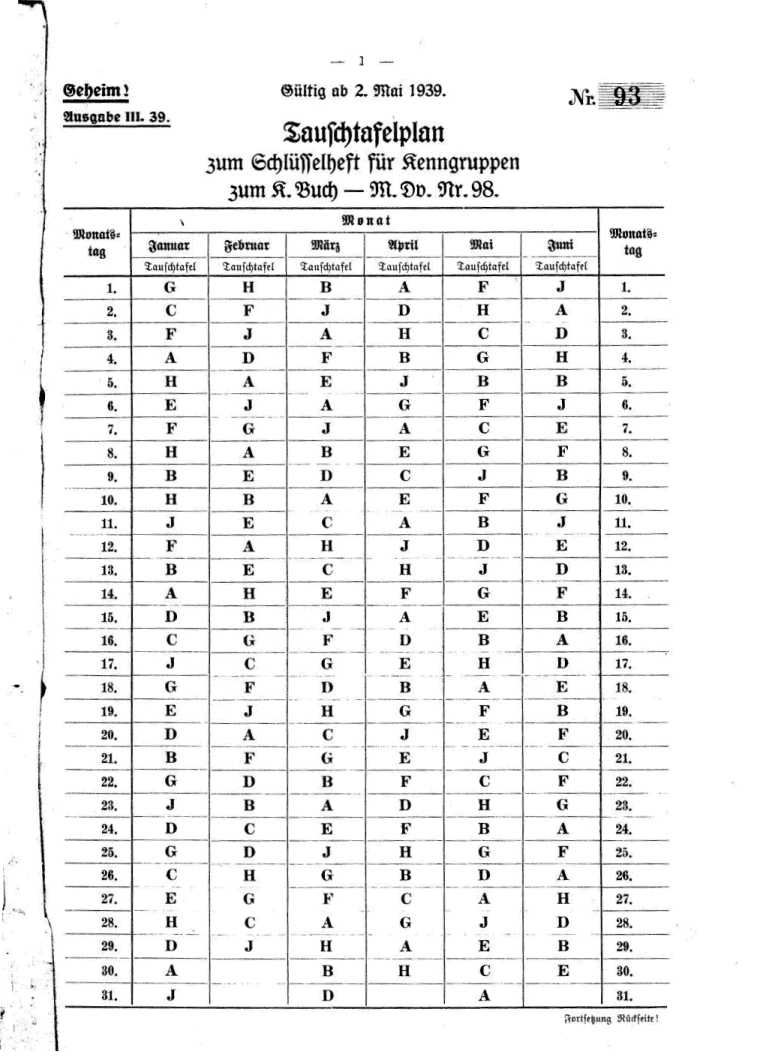
The Kriegsmarine system of Kenngruppen was completely different to the Heer and Luftwaffe Kenngruppen system. In addition to the key sheets, the Kriegsmarine used a Kenngruppenbuch on their main cipher nets to determine the message key. This Kenngruppenbuch is not to be confused with the Kenngruppenheft for Short-signals (see Kurzsignale) which has a completely different purpose. The Kenngruppenbuch contained the following parts:
- Zuteilungsliste (an allotment list) that told the operator which table he should use for a particular cipher net. This list consisted of two parts. The first part showed the table number, given the name of the cipher nets, and the second part showed the different cipher nets, given the table number.
- Tauschtafelplan (table pointer) told the operator which column of a given table was used to select the required trigrams.
- Spalten (columns) with the Kenngruppen (indicator and encryption groups).
The operator had to select two three-letter kenngruppen or trigrams from the Kenngruppenbuch:
- Schlüsselkenngruppe (key indicator group) to identify which key was used.
- Verfahrenkenngruppe (encryption indicator group) to obtain the message key.
Both Schlüsselkenngruppe and Verfahrenkenngruppe had their own tables as determined in the Zuteilungsliste.
With the Enigma in the Grundstellung (the basic position for that day) the operator typed in the Verfahrenkenngruppe. The result would be the message key, used as start position to encipher the message. The two trigrams together (Schlüsselkenngruppe and Verfahrenkenngruppe) were the message indicator.
Finally, this message indicator underwent an additional substitution encryption with a bigram table called Doppelbuchstabentauschtafel or double-letter conversion table (see next section below).
Images of the Kenngruppenbuch (click to enlarge)
The Kriegsmarine Enigma messages were formatted in four-letter groups. Some messages were encoded with the Kurzsignalheft codebook or the Wetterkurzschlüssel, prior to encryption with the Enigma. The Kurzsignalheft (short-signal book) converted words, numbers and all kinds of operational and technical expressions and phrases into four-letter codes. The Wetterkurzschlüssel (weather-short signal key) converted a complete weather report into a 23 or 24 letters code. For more information on Kurzsignale, please read the Kurzsignale procedures page.
The Bigram Table 
The Kriegsmarine message indicator (the Schlüsselkenngruppe and Verfahrenkenngruppe together) were encoded with a bigram table called Doppelbuchstabentauschtafel or double-letter conversion table. A set of bigram tables consisted of nine different tables, labelled A to J. A calendar determined which of the substitution tables was used on a particular day.
The bigram table was reciprocal, meaning that if a bigram AB was encoded in KW, the bigram KW would also decode to AB. The operator wrote the two trigrams from the message indicator underneath each other but added one random dummy letter at the beginning of the first trigram and one dummy letter at the end of the second trigram. To encode, bigrams were taken vertically from the message indicator and encoded according to the bigram table.
As an example, we will encode the message indicator HLG KQK with Bigram Table “Fluss”.
The dummy random letters, in our example A and Z, are added to the trigram Schlüsselkenngruppe HLG and Verfahrenkenngruppe KQK:
AHLG
KQKZ
Bigram encoding with Doppelbuchstabentauschtafel B:
AK=BD HQ=BJ LK=EM GZ=EJ
The resulting message indicator: BDBJ EMEJ
The receiving operator decoded the eight letters of the message indicator with the help of his bigram table. The resulting first trigram would show him the proper key. Next, with the rotors in the Grundstellung, he would type in the second trigram. The resulting trigram was the recovered message key. He would set this message key as rotor positions and finally decipher the rest of the message. The above example was used on the 3-rotor M3 Enigma. The procedure for the four-rotor M4 Enigma was identical but used all four letters instead of three and one random letter.
Typical format of a Kriegmarine message:
|
The message is for BDU, is created at 15h40 on the 8th day, has serial number 107 and consists of 24 groups. At the beginning of the message, we have the message indicator BDBJ EMEJ, which is repeated at the end of the message. The group length of four letters and the repetition of the message indicator at the end were characteristic for naval messages.
The Navy procedure as describe above was used by the main naval cipher areas. Many cipher nets, used in less important areas such as in the Black Sea, Balkan and the Far East didn’t use this complex procedure with the Kenngruppenbuch to select message keys. Instead, they applied the insecure “throw-on” system with double enciphered message key that was abolished by the Wehrmacht in 1940.
Procedures and abbreviations 
The Heer and Luftwaffe transmitted their messages always in five-letter group. To make cryptanalysis harder, it was forbidden to use more than 250 characters in a single message. Longer messages were divided into several parts, each part using its own message key. The Enigma machine could process letters only. Therefore, numbers were written out and punctuations were replaced by rare letter combinations. The Wehrmacht used the following abbreviations:
KLAM = Parenthesis
ZZ = Comma
X = Full stop (end of sentence)
YY = Point or dot
X****X = Inverted commas
Question mark (Fragezeichen in German) was usually abbreviated to FRAGE, FRAGEZ or FRAQ. Foreign names, places, etc. are delimited twice by "X", as in XPARISXPARISX or XFEUERSTEINX. The letters CH were written as Q. ACHT became AQT, RICHTUNG became RIQTUNG.
Numbers were written out as NULL EINZ ZWO DREI VIER FUNF SEQS SIEBEN AQT NEUN
It was prohibited to encipher the word "NULL" several times in succession, so they used CENTA (00), MILLE (000) and MYRIA (0000). Some examples: 200 = ZWO CENTA, 00780 = CENTA SIEBEN AQT NULL.
To make cryptanalysis even harder, some complications were introduced in the Wehrmacht message procedures during the war. Since the third, left-most rotor, only advanced every 676 keystrokes, this rotor didn't have much effect during enciphering (such long messages were forbidden for security reasons). However, the operator could encipher a certain four-letter code into the message, for instance CYOP, and change the left rotor position. When the receiving operator encountered these letters during deciphering, he also turned the left-most rotor to another position (in the case CYOP to position O).
Another complication, added at the end of the war, was placing the rotors 'with rotation'. Every 8 hours, a given rotor placing was rotated clockwise. If the rotors for that day were 241, this changed during the day to 124 and 412. The ring setting for the individual rotors did not change and moved along with the rotors.
The Kriegsmarine formatted their messages in four-letter groups. They used the following abbreviations:
X = Period
Y = Comma
UD = Question Mark
XX = Colon
YY = Dash/Hyphen/Slant
KK**KK = Parenthesis
J******J = Stress Mark
Related information on this site 
- Enigma History
- Technical Details on the Enigma
- Enigma and the U-boat War
- Kurzsignale (Short Signals) on German U-boats
- Break an original M4 message and the story of U-264
- Enigma Cipher Challenge
- Enigma FAQ page
- Enigma Simulator
- Enigma Codebook Tool
More on Enigma Procedures (offsite -
opens in new tab) 
- Enigma Message Procedures Used by the Heer, Luftwaffe and Kriegsmarine My article in Cryptologia Volume 34, Issue 4, Oct 2010, page 329-339.
- The
Kenngruppenbuch Indicator System by Ralph Erskine

- General Procedure for Kriegsmarine Schlüssel M and its Officer and Staff procedure document translations, Tony Sale
- Wehrmacht Enigma Manual and Key Setting Procedures from Bob Lord's website
- Breaking German Wehrmacht Ciphers Project to break a large number of authentic Enigma wartime messages, Frode Weierud
- Modern Breaking of Enigma Ciphertexts Several authentic wartime messages with their key settings, Frode Weierud
- Breaking German Navy Cyphers Michael Hoerenberg's website over breken authentieke Enigma M4 berichten, ontdekt tijdens berging U-534
- Ultra in the Atlantic: U-boat operations from NSA archives on ibiblio.org
- Naval Enigma by Hugh Alexander
- On-line Enigma Key Sheet Generator on Peter's meinEnigma website.
© Dirk Rijmenants 2004. Last changes: 21
December 2022
| Home History |